Enterprise-Scale IoT
IoT augments numerous mundane everyday physical entities (e.g., door locks, thermostats, lights, surveillance cameras) with sensing, actuation, computing, communication and storage capabilities, transforming them into smart objects operated by humans and applications. I have solved a series of IoT problems, ranging from IoT service discovery, access control, routing, to command execution. My IoT research differs from others because I explored enterprise-scale heterogeneous IoT contexts. For example, a university campus may have 10,000s of users and 10,000s of devices (tens of buildings each embedded with thousands of devices); IoT users differ in occupations, teams, departments, and IoT devices vary in types, models, functions, computing/communication/storage performances, installation locations, etc. Existing IoT solutions mostly work for small smart homes but not enterprises, due to the latter’s challenges resulting from large scale and heterogeneity. My research addresses these challenges such that large organizations (e.g., enterprises, universities) can benefit from the booming IoT technology.
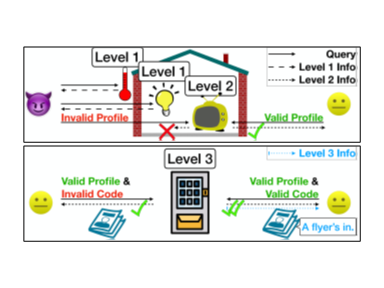
Service Discovery. Which IoT services are around and available, must be discovered by a user’s device first so she can decide which service to access. For security reasons, a service should hide from anyone unauthorized to access it. In enterprise IoT, services are heterogeneous and have various security levels, e.g., thermometers in aisles may be universally disclosed to everyone including visitors, yet equipment in offices should be conditionally revealed to only office members. Existing works are restricted to one-level discovery and ill-matched with enterprise environments. Our Argus system [paper1, paper2] is the first service discovery approach that offers three levels of service visibility in parallel. Three-level discovery cannot be achieved by trivially stapling three existing solutions (each for one level) together because it leads to functional conflict or inefficiency. We solved the challenge in developing a unified system where three levels of discovery cooperate in harmony, with high efficiency and no redundancy. Besides, each level in Argus achieves 10x higher scalability and computational efficiency than alternative solutions.
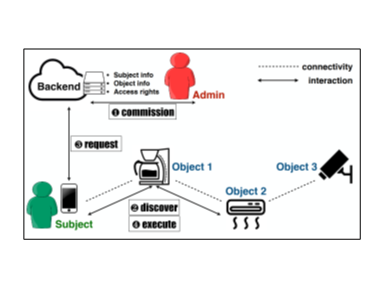
Access Control. IoT services must be accessible to authorized users only, otherwise safety of people and physical assets will be harmed. Enterprise IoT requires fine-grained access control due to its heterogeneous users and devices: given the same device, different users may have different access rights under different contexts (e.g., a janitor may unlock offices only after 10 PM and if nobody is detected to be working inside). It also requires scalable policy updating due to its numerous users, devices and frequent user churns: when a user joins/leaves the organization, the change must be immediately synchronized to the affected IoT devices; otherwise new users will fail to access services timely, while old users continue to access the services they are no longer eligible for. Most existing works target small homes, offer all-or-nothing access (family members have full rights while others have none), take no account of updating scalability, and fail to work in enterprise contexts. Our Heracles system [paper1, paper2] is the first approach to fine-grained access control in enterprise-scale IoT. Also, we addressed the scalability challenge, achieving 10x to 100x higher policy updating efficiency than existing works.
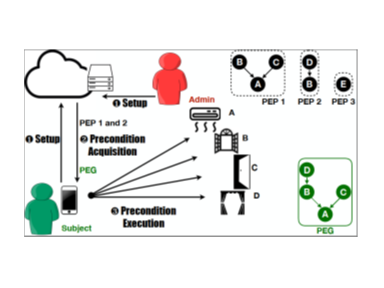
Precondition Execution. There are crucial constraints in IoT that before a command can execute on a device, certain preconditions on other devices must be met first. For example, before a fire sprinkler sprays, the outlets below should be powered off to prevent electric shocks. Our APEX system [paper1, paper2] automatically generates commands to meet all preconditions so the user does not need to manually track or issue those commands one by one, greatly enhancing safety and convenience. It is the first work to define and achieve automatic precondition execution in IoT. There are multiple challenges, e.g., interlaced commands from different users, execution failures. We are the first to identify the similarity between IoT commands and database transactions, and adapt database theory to solve those problems.
360° Video
360° video distinguishes itself from conventional 2D video by having omnidirectional recording and allowing the viewer to choose her viewing direction during video watching. I have been working on various topics of 360° video systems and networking, including 360° video streaming, viewing experience, viewport prediction, viewport recommendation, view synthesis, etc. My 360° video research differs from others because I target more challenging and less studied application scenarios. For example, existing 360° video solutions mostly apply to prerecorded videos but not live/real-time videos, due to the latter’s challenges caused by timing restriction. My research solves these challenges so that many more application scenarios (e.g., live sports, real-time conferencing) can benefit from the emerging 360° video technology.
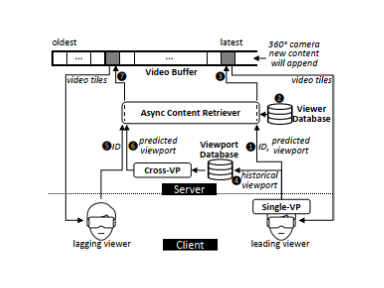
Live Broadcast. A 360° video has a much larger size than a 2D video, and cannot be entirely streamed to low-bandwidth network viewers. Viewport prediction is the mainstream solution to reduce bandwidth cost in 360° video transmission: the server splits a 360° video into small tiles, and only the tiles predicted to be in the viewer’s future viewport will be transmitted with high bitrates. However, most existing solutions only work for videos which have been watched by many viewers, i.e. prerecorded videos but not live broadcast. Our 360BroadView system [paper] is the first work to achieve the same accurate prediction in live broadcast 360° video as in prerecorded video. Besides, we are the first to propose a viewer management approach in this context to address the challenge of prediction accuracy instability caused by viewer churns during live broadcast.